According to the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), cybersecurity threats exploit the increased complexity and connectivity of critical infrastructure systems, placing medical equipment security, patient data and potentially the connected patient at risk. Unfortunately, there is no such thing as a risk-free environment, so HTM teams need to design cybersecurity programs around reducing risks to healthcare technology, and subsequently, to patients and electronic patient health information (ePHI).
Prioritizing Risks for Highest Impact
With so many connected medical devices in the healthcare setting, HTM teams must prioritize where to focus attention to maximize cybersecurity efforts. At Sodexo Healthcare, we prioritize risks in two ways: patient safety and business criticality, where the highest risks are life threatening and the lowest pose no physical threats.
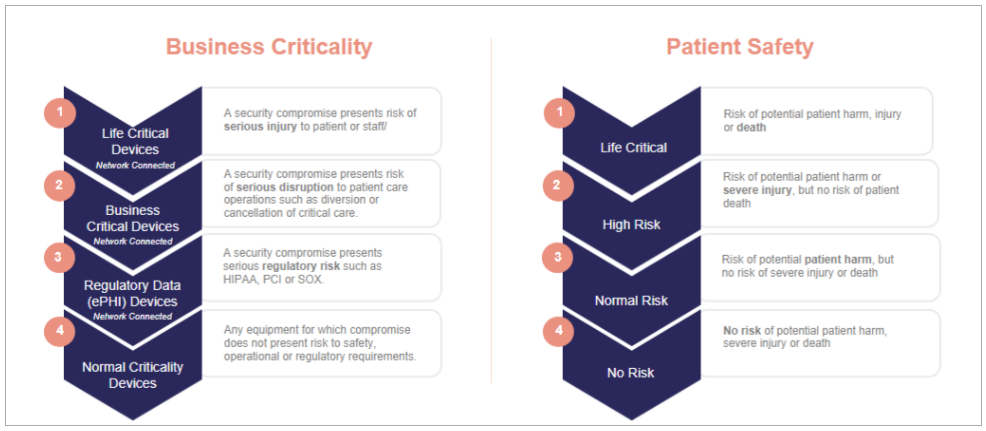
Sodexo Healthcare’s HTM Risk Scale
Data that Informs Priorities
This can only be done by understanding where protected data lives and who has access to it through in-depth data collection. Key data elements that HTM cybersecurity experts should understand to get a full picture of how patient data is stored and moves within the hospital include:
- Whether a device stores information about a single patient or thousands of patients, to help prioritize where the most data lives
- A device’s ability to auto clear patient data, and if that data is being shared across the network
- Safeguarding data through encryption that makes it unreadable if lost or stolen:
- Encryption of data while it is stored on the device
- Encryption of data when it is transmitted across the network
- Use of up-to-date encryption or cryptographic protocols
- Default passwords can be the biggest threat to easy access to data; is the medical device using a default password and can that password be changed?
Reducing risks starts with understanding your inventory and your environment to identify where the vulnerabilities are present. Without a full understanding and the proper processes in place, vulnerabilities turn into risks to assets, data, operations, and ultimately, patient safety. Transitioning from reactive actions to proactive processes is essential for effective risk reduction.
